Featured Access Control
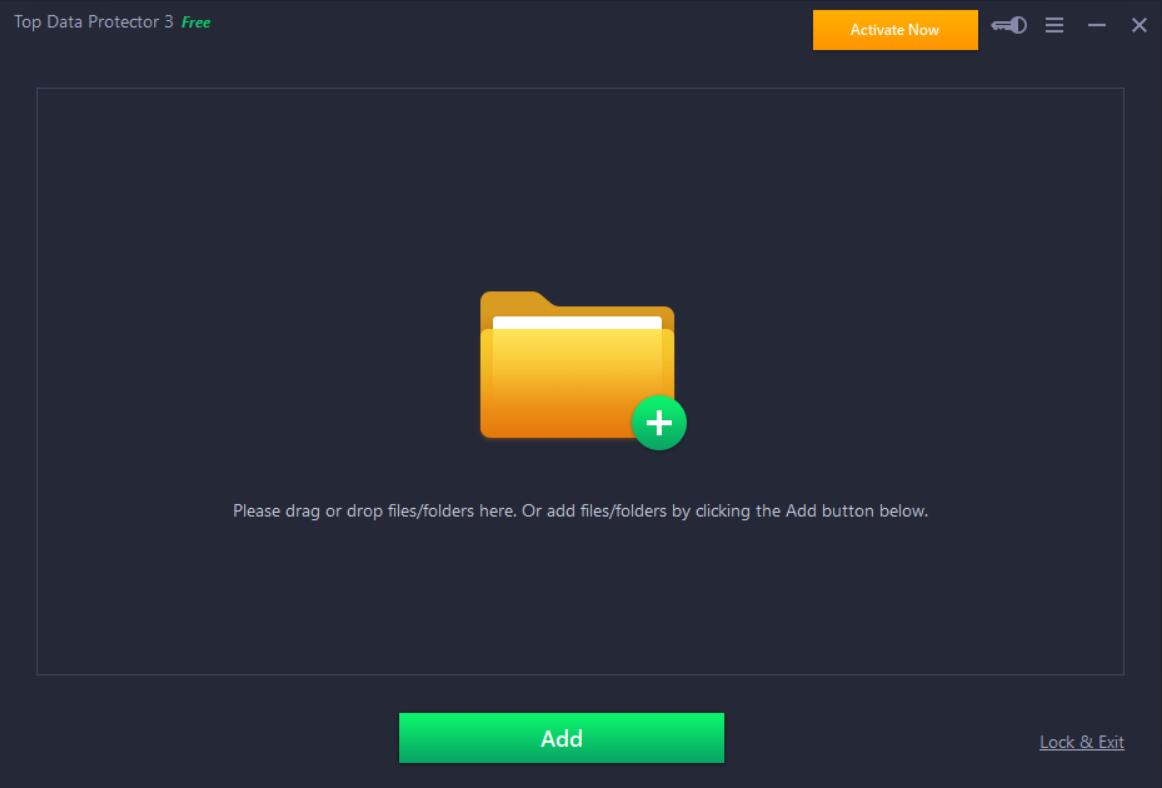
Top Data Protector
Top Data Protector is a lightweight but efficient utility
Read moreMost popular Access Control downloads
Desktop Lock
7.3 downloadDesktop Lock is a computer security protection and access control software product, you can use it to lock computer to prevent people from accessing your private documents and resources. When the computer ...
Windows Firewall Control
6.17.0.0 downloadWindows Firewall Control is a nifty little application which extends the functionality of the Windows Firewall and provides quick access to the most frequent options of Windows Firewall. It runs in the system tray and ...
Lock My PC Free Edition
4.9.5 downloadLock My PC Free Edition is a good and free alternative to standard Win+L Windows lock. The program lets you to lock your computer with a password while you leave it unattended. ...
Windows UAC Manager
2.0 downloadWindows UAC Manager is the free command-line tool to ... or disable User Account Control (UAC) on your Windows system. User Account Control (UAC) is a new security feature (introduced since Vista) that enables users to ...
Security Eye
4.6 download... or send you a email or sms notification. Security Eye is easy to use and extremely reliable for day-to-day operation. Configuration takes only a few minutes, even for a novice. Video ...
Windows USB Blocker
5.0 downloadWindows USB Blocker is the free tool to quickly Block or Unblock USB Storage Devices on any Windows computer USB devices are one of the primary causes ... when you are not around. In such cases, Windows USB Blocker tool will help you to instantly ...
