ShareAlarm 2.2
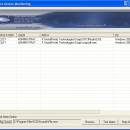
... remote workstation, user, path, OS, permissions of the accessed folder, connection time will available via this tool .The tool is designed with a user-friendly interface and is easy to use.The program have firewall system that allows to block any unwanted connection to your shared resources. ...
| Author | Nsasoft LLC. |
| License | Freeware |
| Price | FREE |
| Released | 2005-10-10 |
| Downloads | 562 |
| Filesize | 444 kB |
| Requirements | 32MB Ram, 1MB free disk |
| Installation | No Install Support |
| Keywords | network tool, network software, net tools, network monitoring, hacking, port scan, network utils, network security, port scanner, intrusion detection, event log, computer security, enterprise security, information security, internet scanner, security software, freeware, shareware |
| Users' rating (11 rating) |
|
| Our rating |

|
Using ShareAlarm Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of ShareAlarm on rapidshare.com, depositfiles.com, megaupload.com etc.
All ShareAlarm download links are direct ShareAlarm full download from publisher site or their selected mirrors.
Avoid: access i oem software, old version, warez, serial, torrent, ShareAlarm keygen, crack.
Consider: ShareAlarm full version, access i full download, premium download, licensed copy.