Internet Traffic Agent 2.9
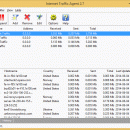
Internet Traffic Agent is an efficient network tool for detailed internet traffic monitoring. It provides daily statistics on local, internet and http traffic of different users. The utility features many advanced functions like capturing the geographical location of any IP-address and the server hostname. This easy-to-use program is designed both for network professionals and usual users and has a user-friendly, easily customized interface. ...
| Author | Flexbyte Software |
| License | Free To Try |
| Price | $29.95 |
| Released | 2017-10-29 |
| Downloads | 1333 |
| Filesize | 2.59 MB |
| Requirements | Windows XP and higher |
| Installation | Install and Uninstall |
| Keywords | internet, traffic, monitor, activity, LAN, TCP/IP, network |
| Users' rating (7 rating) |
Using Internet Traffic Agent Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Internet Traffic Agent on rapidshare.com, depositfiles.com, megaupload.com etc.
All Internet Traffic Agent download links are direct Internet Traffic Agent full download from publisher site or their selected mirrors.
Avoid: activity oem software, old version, warez, serial, torrent, Internet Traffic Agent keygen, crack.
Consider: Internet Traffic Agent full version, activity full download, premium download, licensed copy.