EasyMemo Data/Password Manager 1.4
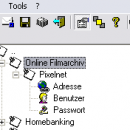
Easy Memo are using steganographie and cryptography as data hiding techniques.<p> Use EasyMemo to organize and securely store files, passwords, pin numbers, usernames, email adreses, web adresses, textstrings and other sensitive information by categories in multi encrypted files (.jrm,.bmp.png). Now you can have a single file or organice your datas in many files. Includes a message blocker, web form filler, crypt service ... ...
| Author | JR-Software |
| License | Free To Try |
| Price | $20.00 |
| Released | 2003-12-12 |
| Downloads | 519 |
| Filesize | 6.37 MB |
| Requirements | |
| Installation | Install and Uninstall |
| Keywords | files, categories, stegano, steganos, data, encrypt, favorites, hackers, information, internet, Kryptographie, organize, password, passwords, restore, securely, sensitive, steganography, store, user, usernames |
| Users' rating (22 rating) |
Using EasyMemo Data/Password Manager Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of EasyMemo Data/Password Manager on rapidshare.com, depositfiles.com, megaupload.com etc.
All EasyMemo Data/Password Manager download links are direct EasyMemo Data/Password Manager full download from publisher site or their selected mirrors.
Avoid: algorithm 5 oem software, old version, warez, serial, torrent, EasyMemo Data/Password Manager keygen, crack.
Consider: EasyMemo Data/Password Manager full version, algorithm 5 full download, premium download, licensed copy.