ThreatSentry 4.0.25.0
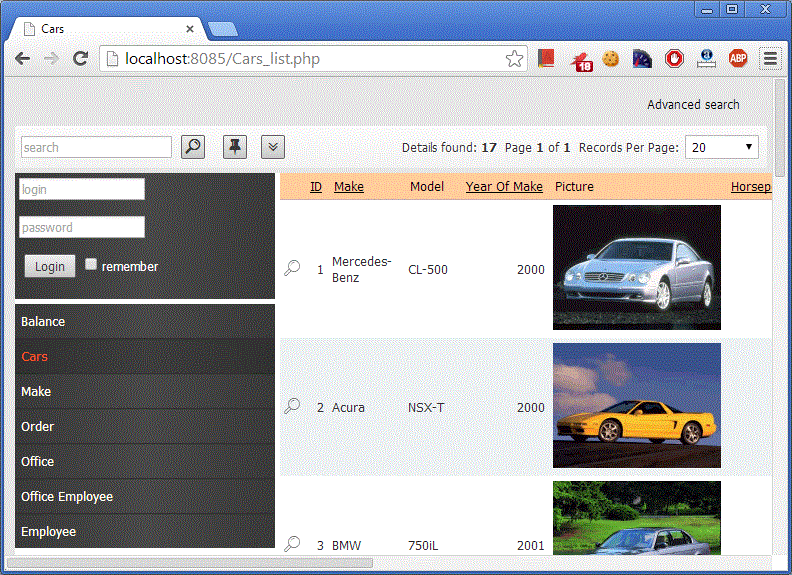
ThreatSentry Windows Web server Host Intrusion Prevention software defends IIS against new and progressive attack techniques, protects network weak points, overcomes lapses in patch management, and reinforces regulatory compliance. An ISAPI filter hosted in MMC, ThreatSentry compares server requests to a knowledgebase and an evolving system baseline to detect untrusted activity and prevent attacks on Microsoft IIS. ...
| Author | Privacyware |
| License | Demo |
| Price | $649.00 |
| Released | 2010-06-30 |
| Downloads | 392 |
| Filesize | 10.50 MB |
| Requirements | |
| Installation | Instal And Uninstall |
| Keywords | Intrusion Prevention, regulatory compliance, IIS server, IIS, Intrusion, Prevention |
| Users' rating (25 rating) |
Using ThreatSentry Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of ThreatSentry on rapidshare.com, depositfiles.com, megaupload.com etc.
All ThreatSentry download links are direct ThreatSentry full download from publisher site or their selected mirrors.
Avoid: audit oem software, old version, warez, serial, torrent, ThreatSentry keygen, crack.
Consider: ThreatSentry full version, audit full download, premium download, licensed copy.