IAP Desktop 2.45.1717
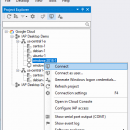
IAP Desktop, developed by Google Cloud Platform, is a powerful tool designed for secure access to your Google Cloud resources. It simplifies the process of connecting to virtual machines and other services behind Identity-Aware Proxy (IAP), providing a seamless user experience. With its intuitive interface, users can easily manage SSH connections, streamline workflows, and enhance security. Ideal for developers and IT professionals, IAP Desktop ensures efficient access while maintaining robust s ... ...
| Author | Google Cloud Platform |
| License | Open Source |
| Price | FREE |
| Released | 2025-02-20 |
| Downloads | 33 |
| Filesize | 4.10 MB |
| Requirements | |
| Installation | |
| Keywords | IAP Desktop, download IAP Desktop, IAP Desktop free download, Connect to VM, Virtual Machine, Google VM, Virtual, Machine, Google, Cloud |
| Users' rating (7 rating) |
Using IAP Desktop Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of IAP Desktop on rapidshare.com, depositfiles.com, megaupload.com etc.
All IAP Desktop download links are direct IAP Desktop full download from publisher site or their selected mirrors.
Avoid: authorized oem software, old version, warez, serial, torrent, IAP Desktop keygen, crack.
Consider: IAP Desktop full version, authorized full download, premium download, licensed copy.