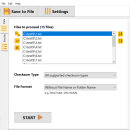
Metamorphosec Checksum File Creator 5.0.0
Metamorphosec Checksum File Creator is a powerful tool designed for generating and managing checksums with ease. Ideal for ensuring file integrity, this software supports multiple algorithms, including MD5, SHA-1, and SHA-256, allowing users to verify data authenticity effortlessly. Its intuitive interface simplifies the checksum creation process, making it accessible for both novices and experts. With batch processing capabilities, users can efficiently handle multiple files, enhancing producti ... ...
| Author | Metamorfosec |
| License | Demo |
| Price | FREE |
| Released | 2025-02-17 |
| Downloads | 79 |
| Filesize | 14.30 MB |
| Requirements | |
| Installation | |
| Keywords | checksum generator, Creator, generate, hash generator, Software, Metamorphosec, File, Checksum, Security, view hash, hash, generator |
| Users' rating (8 rating) |
Using Metamorphosec Checksum File Creator Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Metamorphosec Checksum File Creator on rapidshare.com, depositfiles.com, megaupload.com etc.
All Metamorphosec Checksum File Creator download links are direct Metamorphosec Checksum File Creator full download from publisher site or their selected mirrors.
Avoid: best practices oem software, old version, warez, serial, torrent, Metamorphosec Checksum File Creator keygen, crack.
Consider: Metamorphosec Checksum File Creator full version, best practices full download, premium download, licensed copy.