Svchost Process Analyzer 1.3
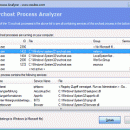
The free Svchost Process Analyzer examines all Svchost instances. This makes it easy to recognize processes that start up through Svchost and disguise their activities. This was the way the Conficker Worm, which infected millions of computers, operated. The genuine Svchost.exe is an important Windows system process and is located in the C:WindowsSystem32 directory. The Svchost.exe processis often misused by spyware, Trojans or worms. ...
| Author | A. & M. Neuber Software |
| License | Freeware |
| Price | FREE |
| Released | 2017-02-16 |
| Downloads | 150 |
| Filesize | 523 kB |
| Requirements | - |
| Installation | No Install Support |
| Keywords | svchost, svchost.exe, conficker, configer worm, svhost, scvhost, _svchost.exe |
| Users' rating (7 rating) |
Using Svchost Process Analyzer Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Svchost Process Analyzer on rapidshare.com, depositfiles.com, megaupload.com etc.
All Svchost Process Analyzer download links are direct Svchost Process Analyzer full download from publisher site or their selected mirrors.
Avoid: blocked oem software, old version, warez, serial, torrent, Svchost Process Analyzer keygen, crack.
Consider: Svchost Process Analyzer full version, blocked full download, premium download, licensed copy.