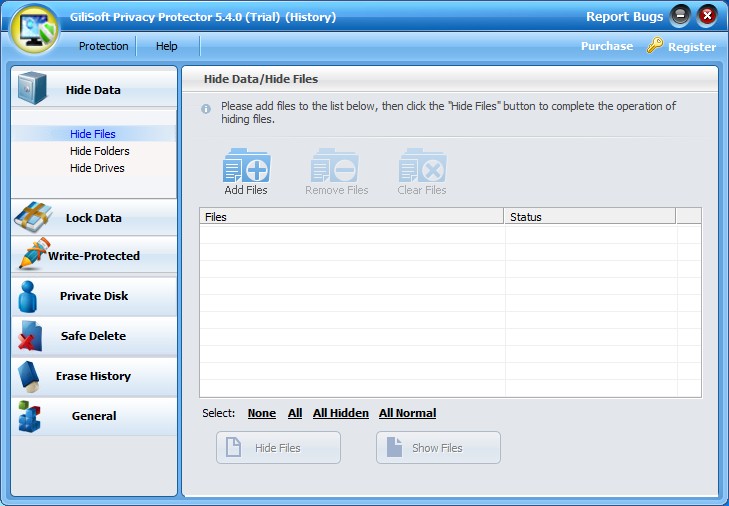
Nym Connect 1.1.21
Nym Connect, developed by NYM, is a cutting-edge privacy-focused software designed to enhance your online security and anonymity. By leveraging advanced mixnet technology, it effectively obscures your internet traffic, making it nearly impossible to trace back to you. The user-friendly interface ensures seamless integration into your daily browsing experience, while robust encryption safeguards your data from prying eyes. Ideal for privacy advocates and everyday users alike, Nym Connect empowers ... ...
| Author | NYM |
| License | Open Source |
| Price | FREE |
| Released | 2024-11-18 |
| Downloads | 25 |
| Filesize | 12.90 MB |
| Requirements | |
| Installation | |
| Keywords | Nym Connect, download Nym Connect, Nym Connect free download, Decentralized Web, Online Privacy, Online Anonimity, decentralized, privacy, anonymity, network |
| Users' rating (7 rating) |
Using Nym Connect Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Nym Connect on rapidshare.com, depositfiles.com, megaupload.com etc.
All Nym Connect download links are direct Nym Connect full download from publisher site or their selected mirrors.
Avoid: built in resources oem software, old version, warez, serial, torrent, Nym Connect keygen, crack.
Consider: Nym Connect full version, built in resources full download, premium download, licensed copy.