Ace File Shredder 1.1
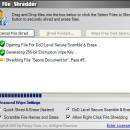
Did you know deleted files can easily be recovered using file undelete utilities? Prevent your deleted files or sensitive data from being recovered with our fast and efficient digital file shredder, able to shred files, folders, and wipe free disk space to prevent previously deleted files from being recovered. Some features include Drag & Drop File/Folder support, Right-Click file menu shredding, and free disk space wipe and erase. ...
| Author | My Privacy Tools, Inc. |
| License | Commercial |
| Price | $14.95 |
| Released | 2007-04-18 |
| Downloads | 821 |
| Filesize | 755 kB |
| Requirements | |
| Installation | Install and Uninstall |
| Keywords | file, shredder, digital, erase, encrypt, secure, wipe, free, space, disk, unused, slack, recover, undelete, data, scramble, dod, department, defense, standard, encryption, properties, wiper |
| Users' rating (15 rating) |
Using Ace File Shredder Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Ace File Shredder on rapidshare.com, depositfiles.com, megaupload.com etc.
All Ace File Shredder download links are direct Ace File Shredder full download from publisher site or their selected mirrors.
Avoid: encrypt oem software, old version, warez, serial, torrent, Ace File Shredder keygen, crack.
Consider: Ace File Shredder full version, encrypt full download, premium download, licensed copy.