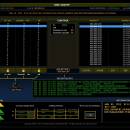
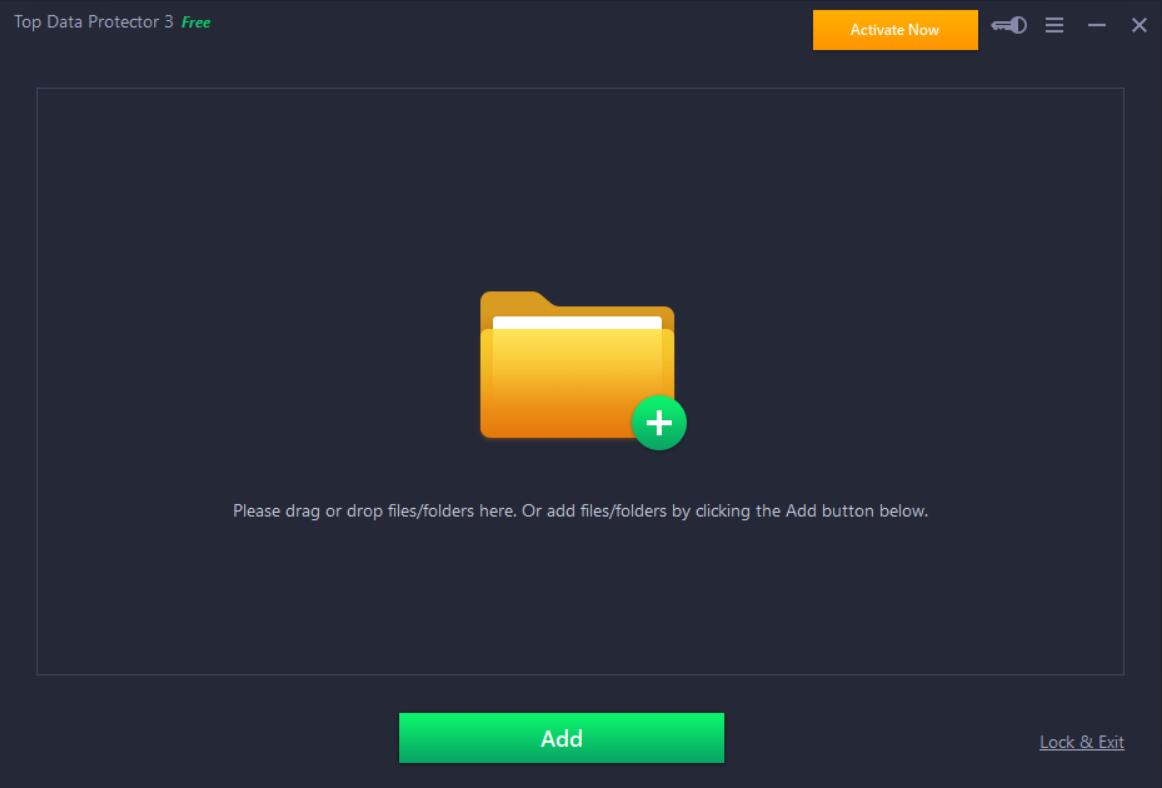
USB Lock RP 13.924
USB Lock RP by Advanced Systems is a robust security solution designed to protect sensitive data from unauthorized access via USB ports. This software enables administrators to control and restrict USB device usage, ensuring that only approved devices can connect to the system. With an intuitive interface, it offers real-time monitoring, detailed reporting, and customizable policies to suit various organizational needs. Ideal for businesses seeking to enhance data security, USB Lock RP effective ... ...
| Author | Advanced Systems |
| License | Demo |
| Price | FREE |
| Released | 2025-02-20 |
| Downloads | 760 |
| Filesize | 24.80 MB |
| Requirements | |
| Installation | Instal And Uninstall |
| Keywords | Protect, device control, data protection, removable media, access management, Lock USB, Authorize, USB Lock, USB Protector, USB Lock RP, USB, USB security, Lock |
| Users' rating (46 rating) |
Using USB Lock RP Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of USB Lock RP on rapidshare.com, depositfiles.com, megaupload.com etc.
All USB Lock RP download links are direct USB Lock RP full download from publisher site or their selected mirrors.
Avoid: enforce oem software, old version, warez, serial, torrent, USB Lock RP keygen, crack.
Consider: USB Lock RP full version, enforce full download, premium download, licensed copy.