Omega DB Security Reporter 2.4.0
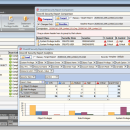
Security audit assessment and software-only solution for Oracle databases. Security Reporting on Oracle database for: Privileges - System Privileges, Object Privileges and Role Privileges; Audits: System Privileges, User Statements and Object Privileges; Others: User Password Profile Resources and Initialization Parameters (security related). ...
| Author | DATAPLUS |
| License | Free To Try |
| Price | $899.00 |
| Released | 2023-07-10 |
| Downloads | 100 |
| Filesize | 88.96 MB |
| Requirements | Oracle Database: 10g R2 and above. Application:Windows |
| Installation | Install and Uninstall |
| Keywords | oracle, database, security, compliance, assess, report, scan, audit, privilege, user, object, data |
| Users' rating (19 rating) |
Using Omega DB Security Reporter Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Omega DB Security Reporter on rapidshare.com, depositfiles.com, megaupload.com etc.
All Omega DB Security Reporter download links are direct Omega DB Security Reporter full download from publisher site or their selected mirrors.
Avoid: evaluation oem software, old version, warez, serial, torrent, Omega DB Security Reporter keygen, crack.
Consider: Omega DB Security Reporter full version, evaluation full download, premium download, licensed copy.