Ascendant NFM 1.61
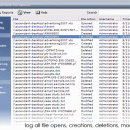
Ascendant NFM represents the latest in cutting-edge network file monitoring security software and asset protection. While requiring absolutely no software installation on any computer on your network you can centrally monitor and record every single file action, application execution, and website visit that occurs on your network. Every file creation, modification, and deletion is recorded along with the user that performed the action, and when. ...
| Author | Ascendant Security |
| License | Commercial |
| Price | $69.95 |
| Released | 2011-01-04 |
| Downloads | 518 |
| Filesize | 606 kB |
| Requirements | 2MB Disk Space, Admin Privileges, File Sharing Enabled |
| Installation | Install and Uninstall |
| Keywords | Network Monitoring, File Monitoring, Network Security, Asset Protection, Employee Monitoring, Data Security |
| Users' rating (9 rating) |
Using Ascendant NFM Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Ascendant NFM on rapidshare.com, depositfiles.com, megaupload.com etc.
All Ascendant NFM download links are direct Ascendant NFM full download from publisher site or their selected mirrors.
Avoid: event log client oem software, old version, warez, serial, torrent, Ascendant NFM keygen, crack.
Consider: Ascendant NFM full version, event log client full download, premium download, licensed copy.