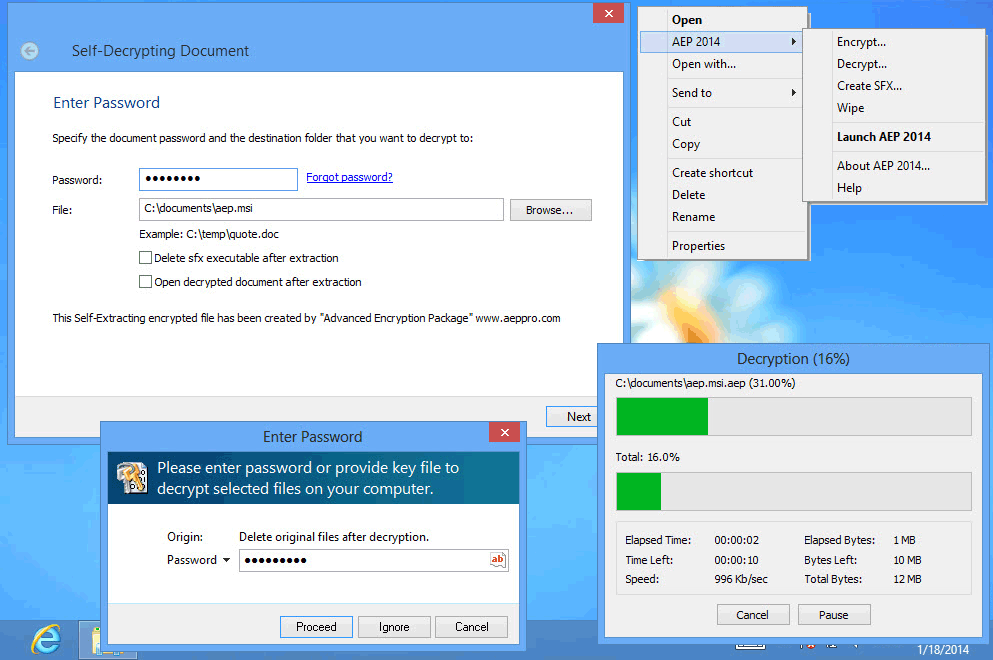
ArmorTools 25.4.1
ArmorTools is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites... ...
| Author | WinTools Software Engineering |
| License | Free To Try |
| Price | $24.99 |
| Released | 2025-04-08 |
| Downloads | 129 |
| Filesize | 859 kB |
| Requirements | MS Windows, 1024x768 resolution, 16Mb free space |
| Installation | Install and Uninstall |
| Keywords | encryption, virtual disk, encrypt, security, shredder, cleaner, disk, disks, windows, encrypted disk, encrypted, shred, tweak, privacy, code, extra disks, disks |
| Users' rating (12 rating) |
Using ArmorTools Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of ArmorTools on rapidshare.com, depositfiles.com, megaupload.com etc.
All ArmorTools download links are direct ArmorTools full download from publisher site or their selected mirrors.
Avoid: example code oem software, old version, warez, serial, torrent, ArmorTools keygen, crack.
Consider: ArmorTools full version, example code full download, premium download, licensed copy.