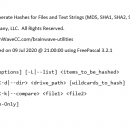
FileHash 5.3.0.1281
FileHash by BrainWave Consulting Company, LLC is a powerful utility designed for users who need to verify file integrity and authenticity. With its intuitive interface, FileHash allows you to generate and compare hash values effortlessly, ensuring that your files remain unaltered during transfers or storage. Supporting multiple ... Whether you’re safeguarding sensitive data or managing large file collections, FileHash deli ... ...
| Author | BrainWave Consulting Company, LLC |
| License | Freeware |
| Price | FREE |
| Released | 2025-05-05 |
| Downloads | 24 |
| Filesize | 686 kB |
| Requirements | |
| Installation | |
| Keywords | FileHash, download FileHash, FileHash free download, generate hash, hash generator, checksum generator, hash, checksum, MD5, encryption |
| Users' rating (8 rating) |
Using FileHash Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of FileHash on rapidshare.com, depositfiles.com, megaupload.com etc.
All FileHash download links are direct FileHash full download from publisher site or their selected mirrors.
Avoid: file backups oem software, old version, warez, serial, torrent, FileHash keygen, crack.
Consider: FileHash full version, file backups full download, premium download, licensed copy.