Digital Forensic Examiner Tool 1.3
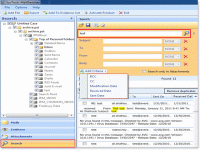
Digital forensic examiner tool mainly consists of the term “computer forensics” as it basically deals in forensic recovery of digital evidences. Forensic evidence collection and analysis both are major features of digital data analysis tool, they both plays a vital role while doing the forensic examination of digital evidences by analyzing the forensic evidence and if the evidence is worthy for the case, by collecting the forensic evidence. ...
| Author | Digital Forensic Examiner |
| License | Free To Try |
| Price | $299.00 |
| Released | 2013-03-12 |
| Downloads | 192 |
| Filesize | 13.90 MB |
| Requirements | Pentium II 400 MHz, 64 MB RAM, Minimum 10 MB Space |
| Installation | Install and Uninstall |
| Keywords | digital forensic examiner, digital data analysis |
| Users' rating (9 rating) |
Using Digital Forensic Examiner Tool Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Digital Forensic Examiner Tool on rapidshare.com, depositfiles.com, megaupload.com etc.
All Digital Forensic Examiner Tool download links are direct Digital Forensic Examiner Tool full download from publisher site or their selected mirrors.
Avoid: hide html oem software, old version, warez, serial, torrent, Digital Forensic Examiner Tool keygen, crack.
Consider: Digital Forensic Examiner Tool full version, hide html full download, premium download, licensed copy.