Deletor 5.13
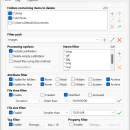
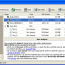
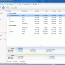
Deletor helps you reduce the clutter in your disks and other storage media by deleting files and folders matching your criteria. The program can search multiple root folders and delete files according to their tags, metadata, time, duration, size, attributes, name and name patterns including wildcards. A shredding feature is also available to destroy sensitive documents and make them virtually impossible to recover. ...
| Author | Basta Computing, Inc. |
| License | Free To Try |
| Price | $19.95 |
| Released | 2023-06-27 |
| Downloads | 338 |
| Filesize | 5.64 MB |
| Requirements | 10MB of free disk space |
| Installation | Install and Uninstall |
| Keywords | Basta, Deletor, delete, shred, erase, wipe, files, folders, sensitive, data, secure, batch, remove, cache, destroy, purge, schedule, filter, tag, metadata, command line, cli, cmd |
| Users' rating (20 rating) |
Using Deletor Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Deletor on rapidshare.com, depositfiles.com, megaupload.com etc.
All Deletor download links are direct Deletor full download from publisher site or their selected mirrors.
Avoid: in line oem software, old version, warez, serial, torrent, Deletor keygen, crack.
Consider: Deletor full version, in line full download, premium download, licensed copy.