Wise Undelete Files 2.6.6
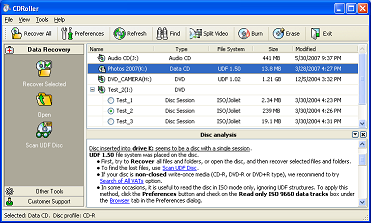
Wise Undelete Files is a good program to undelete pictures, photos and videos. Images undeleting is a risky task since it may lead to permanent data loss. But with the help of Wise Undelete Files, you can take it easy. Wise Undelete Files can undelete all kinds of lost data without any risk. You can also preview the pictures you want to recover before you recover them. ...
| Author | LionSea Software inc |
| License | Free To Try |
| Price | $49.97 |
| Released | 2013-04-18 |
| Downloads | 128 |
| Filesize | 7.76 MB |
| Requirements | Minimum 500MHz CPU, 512MB RAM, and 2GBMB hard drive space |
| Installation | Install and Uninstall |
| Keywords | how to Undelete Files, restore Undelete Files, Undelete Files recovering, recovering Undelete Files |
| Users' rating (10 rating) |
Using Wise Undelete Files Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Wise Undelete Files on rapidshare.com, depositfiles.com, megaupload.com etc.
All Wise Undelete Files download links are direct Wise Undelete Files full download from publisher site or their selected mirrors.
Avoid: limitation of use oem software, old version, warez, serial, torrent, Wise Undelete Files keygen, crack.
Consider: Wise Undelete Files full version, limitation of use full download, premium download, licensed copy.