Apeaksoft iPhone Eraser for Mac 1.0.20
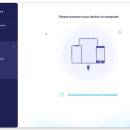
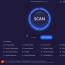
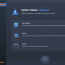
If your iOS devices memory is full and you want to clean up for more free space, Apeaksoft iPhone Eraser for Mac is your best choice. It could help you delete junk files and large files, uninstall applications, manage your photos. If you want to erase all the data in your device, you could use the Erase All Data function to wipe all the data permanently. ...
| Author | Apeaksoft Studio |
| License | Free To Try |
| Price | $19.96 |
| Released | 2023-11-20 |
| Downloads | 75 |
| Filesize | 27.39 MB |
| Requirements | Processor: 1GHz Intel® processor and Apple M1/M2 chip, 1G RAM or more |
| Installation | Install and Uninstall |
| Keywords | Wipe data, delete large files, clean iOS devices |
| Users' rating (4 rating) |
Using Apeaksoft iPhone Eraser for Mac Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Apeaksoft iPhone Eraser for Mac on rapidshare.com, depositfiles.com, megaupload.com etc.
All Apeaksoft iPhone Eraser for Mac download links are direct Apeaksoft iPhone Eraser for Mac full download from publisher site or their selected mirrors.
Avoid: log on oem software, old version, warez, serial, torrent, Apeaksoft iPhone Eraser for Mac keygen, crack.
Consider: Apeaksoft iPhone Eraser for Mac full version, log on full download, premium download, licensed copy.