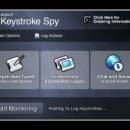
Keystroke Spy 8.52
... - SpyAgent. Keystroke Spy, while being able to log all keystrokes typed by users without them knowing, can also be set to log keystrokes typed only in specific applications. ...
| Author | Spytech |
| License | Free To Try |
| Price | $49.95 |
| Released | 2017-05-22 |
| Downloads | 195 |
| Filesize | 1.25 MB |
| Requirements | Pentium Class PC (133mhz or higher); 2MB Hard disk space |
| Installation | Install and Uninstall |
| Keywords | computer monitoring, parental control, internet monitor, activity recorder, employee monitoring, keylogger, surveillance, PC monitoring, network surveillance, pc spy, remote spy, spy, recorder, keystroke logger, cheating spouse, remote administration |
| Users' rating (16 rating) |
Using Keystroke Spy Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Keystroke Spy on rapidshare.com, depositfiles.com, megaupload.com etc.
All Keystroke Spy download links are direct Keystroke Spy full download from publisher site or their selected mirrors.
Avoid: log oem software, old version, warez, serial, torrent, Keystroke Spy keygen, crack.
Consider: Keystroke Spy full version, log full download, premium download, licensed copy.