Tockler 3.22.2
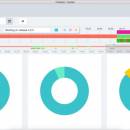
Tockler, developed by MayGo, is an innovative time-tracking tool designed to enhance productivity and streamline workflow management. With its intuitive interface, Tockler allows users to effortlessly log hours, categorize tasks, and generate insightful reports. The software's seamless integration with popular project management platforms makes it a versatile choice for teams of all sizes. Whether you're a freelancer or part of a larger organization, Tockler empowers you to take control of your ... ...
| Author | MayGo |
| License | Open Source |
| Price | FREE |
| Released | 2024-12-03 |
| Downloads | 6 |
| Filesize | 213.00 MB |
| Requirements | |
| Installation | |
| Keywords | download Tockler, Activity, automation, MayGo, Tockler, Timer, Idle, project management, Time Tracker, GitHub, software, Activity Tracker, Tracker, Track Idle Time, Tockler free download |
| Users' rating (7 rating) |
Using Tockler Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Tockler on rapidshare.com, depositfiles.com, megaupload.com etc.
All Tockler download links are direct Tockler full download from publisher site or their selected mirrors.
Avoid: patterns oem software, old version, warez, serial, torrent, Tockler keygen, crack.
Consider: Tockler full version, patterns full download, premium download, licensed copy.