Eltima Serial Splitter Mobile 3.0
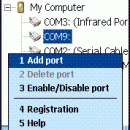
Serial Splitter Mobile by Eltima is useful if you need several applications to work with the same serial port on your mobile device simultaneously. Finally, one program works with one virtual port, the other one with another port and so on, but in fact all of them work with the same split real port. It enables data exchange between applications, which can be used in GPS simulation systems. ...
| Author | Virtual Serial Port Software |
| License | Free To Try |
| Price | $49.95 |
| Released | 2007-07-06 |
| Downloads | 302 |
| Filesize | 7.59 MB |
| Requirements | Microsoft Windows Mobile 2003/2005 |
| Installation | Install and Uninstall |
| Keywords | split real ports on mobile device, virtual com port, share serial port, gps splitter mobile, disable serial ports |
| Users' rating (7 rating) |
Using Eltima Serial Splitter Mobile Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Eltima Serial Splitter Mobile on rapidshare.com, depositfiles.com, megaupload.com etc.
All Eltima Serial Splitter Mobile download links are direct Eltima Serial Splitter Mobile full download from publisher site or their selected mirrors.
Avoid: read only oem software, old version, warez, serial, torrent, Eltima Serial Splitter Mobile keygen, crack.
Consider: Eltima Serial Splitter Mobile full version, read only full download, premium download, licensed copy.