REFOG Mac Keylogger 3.0
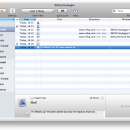
... from family computer activities. Users worried about the safety of their children from Internet predators or of the sanctity of their marriage from cheating spouses can use this keylogger for Mac to monitor a comprehensive history of visited sites, opened applications, and typed messages without the user even knowing the software has been installed. ...
| Author | REFOG |
| License | Free To Try |
| Price | $49.95 |
| Released | 2014-08-07 |
| Downloads | 264 |
| Filesize | 4.60 MB |
| Requirements | Keylogger for Mac is now logging visited web pages |
| Installation | Install and Uninstall |
| Keywords | keylogger for mac, mac keylogger, keylogger mac |
| Users' rating (20 rating) |
Using REFOG Mac Keylogger Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of REFOG Mac Keylogger on rapidshare.com, depositfiles.com, megaupload.com etc.
All REFOG Mac Keylogger download links are direct REFOG Mac Keylogger full download from publisher site or their selected mirrors.
Avoid: safe internet oem software, old version, warez, serial, torrent, REFOG Mac Keylogger keygen, crack.
Consider: REFOG Mac Keylogger full version, safe internet full download, premium download, licensed copy.