Hard_Configurator 7.0.0.0
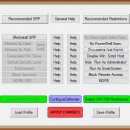
Hard_Configurator by AndyFul is a versatile software tool designed to streamline the configuration of hardware components. With an intuitive interface, it simplifies the process of managing settings for various devices, enhancing performance and compatibility. The software supports a wide range of hardware, making it ideal for both novice users and seasoned tech enthusiasts. Its robust features, including real-time monitoring and easy customization options, empower users to optimize their system ... ...
| Author | AndyFul |
| License | Freeware |
| Price | FREE |
| Released | 2024-09-18 |
| Downloads | 13 |
| Filesize | 21.90 MB |
| Requirements | |
| Installation | |
| Keywords | SRP manager, Hard_Configurator, manage restriction, policy, AndyFul, restriction, tool, configuration, SRP, GitHub, download Hard_Configurator, software, manage SRP, Software Restriction Policies |
| Users' rating (11 rating) |
Using Hard_Configurator Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Hard_Configurator on rapidshare.com, depositfiles.com, megaupload.com etc.
All Hard_Configurator download links are direct Hard_Configurator full download from publisher site or their selected mirrors.
Avoid: security posture oem software, old version, warez, serial, torrent, Hard_Configurator keygen, crack.
Consider: Hard_Configurator full version, security posture full download, premium download, licensed copy.