Web Proxy EH-1.3.6
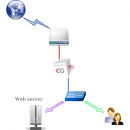
CG Web Proxy allows you to Secure and Optimize the Web traffic. It can be implemented in forwarding mode for Web users or in reverse mode for Web applications. CG Web Proxy can be powered by an antivirus, a Web cache, a Web traffic compression facility, a Web traffic logger, a URL filtering facility and a WAF (Web Application Firewall). ...
| Author | CacheGuard Technologies Ltd |
| License | Free To Try |
| Price | $9.99 |
| Released | 2017-03-09 |
| Downloads | 200 |
| Filesize | 185.83 MB |
| Requirements | Dedicated x84/x64 based Hardware or Virtual Machine with at least 1.5 GB RAM, 16 GB HDD and 2xNIC. |
| Installation | Install and Uninstall |
| Keywords | web proxy, http proxy, https proxy, reverse proxy |
| Users' rating (9 rating) |
Using Web Proxy Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Web Proxy on rapidshare.com, depositfiles.com, megaupload.com etc.
All Web Proxy download links are direct Web Proxy full download from publisher site or their selected mirrors.
Avoid: shareware oem software, old version, warez, serial, torrent, Web Proxy keygen, crack.
Consider: Web Proxy full version, shareware full download, premium download, licensed copy.