Plain Sight 1.0
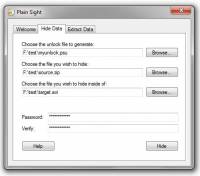
... to hide files within other files using military strength 256 bit AES encryption.
For example you can hide your passwords inside your favorite vacation photo. The file you choose to hide inside of remains functional, for example, if you hide inside an image, the image still opens, prints, and looks the same. The only difference is the file size.
When you hide data, an Unlock file is generated, that file along with your p ...
| Author | Void Realms LLC |
| License | Freeware |
| Price | FREE |
| Released | 2009-12-25 |
| Downloads | 211 |
| Filesize | 532 kB |
| Requirements | |
| Installation | Instal And Uninstall |
| Keywords | security, privac, password, encryption, file |
| Users' rating (2 rating) |
Using Plain Sight Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Plain Sight on rapidshare.com, depositfiles.com, megaupload.com etc.
All Plain Sight download links are direct Plain Sight full download from publisher site or their selected mirrors.
Avoid: strength oem software, old version, warez, serial, torrent, Plain Sight keygen, crack.
Consider: Plain Sight full version, strength full download, premium download, licensed copy.