Portable BleachBit 5.0.0
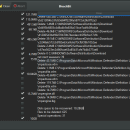
Portable BleachBit, developed by Andrew Ziem, is a powerful, open-source tool designed for privacy-conscious users seeking to free up disk space and enhance system performance. This lightweight application allows you to securely delete unnecessary files, clear browser caches, and erase sensitive data without leaving traces. Its portable nature means it can be run from a USB drive, making it ideal for on-the-go maintenance. With a user-friendly interface and extensive customization options, Porta ... ...
| Author | Andrew Ziem |
| License | Open Source |
| Price | FREE |
| Released | 2025-05-02 |
| Downloads | 552 |
| Filesize | 19.50 MB |
| Requirements | |
| Installation | Instal And Uninstall |
| Keywords | Portable BleachBit, system cleaner, cache, wipe, delete |
| Users' rating (29 rating) |
Using Portable BleachBit Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Portable BleachBit on rapidshare.com, depositfiles.com, megaupload.com etc.
All Portable BleachBit download links are direct Portable BleachBit full download from publisher site or their selected mirrors.
Avoid: unauthorized oem software, old version, warez, serial, torrent, Portable BleachBit keygen, crack.
Consider: Portable BleachBit full version, unauthorized full download, premium download, licensed copy.