SysExpertez 3.4
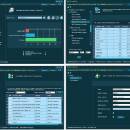
Managing IT networks is a challenge due its dynamic nature. Lack of awareness makes the network harder to manage and secure, because what you don't know can hurt you! Do you know the number PCs / servers and devices, hardware and software, users and groups, user activities in your network? You need something that works automatically and provides the information you need, so that you can take appropriate actions. ...
| Author | SARANGSoft Corporation |
| License | Free To Try |
| Price | $99.95 |
| Released | 2017-12-05 |
| Downloads | 82 |
| Filesize | 32.55 MB |
| Requirements | SysExpertez Server: Windows VISTA or later, SQL Server Expr 2008 or later. Agent:Windows XP or later |
| Installation | Install and Uninstall |
| Keywords | IT Asset Management, Active Directory Network Management, Non-Windows Device Detection, Network Asset Tracking, Hardware Assets, Software Asset |
| Users' rating (6 rating) |
Using SysExpertez Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of SysExpertez on rapidshare.com, depositfiles.com, megaupload.com etc.
All SysExpertez download links are direct SysExpertez full download from publisher site or their selected mirrors.
Avoid: unwanted oem software, old version, warez, serial, torrent, SysExpertez keygen, crack.
Consider: SysExpertez full version, unwanted full download, premium download, licensed copy.