IP-Sniff 5.8.5.2174
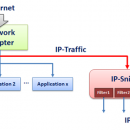
... and analyze IP traffic in real-time, identifying potential vulnerabilities and unauthorized access. The software features advanced filtering options, customizable alerts, and comprehensive reporting capabilities, making it an essential asset for maintaining network integrity. Whether you're managing a small office or a ... ...
| Author | decontev |
| License | Open Source |
| Price | FREE |
| Released | 2024-12-04 |
| Downloads | 22 |
| Filesize | 451 kB |
| Requirements | |
| Installation | |
| Keywords | IP-Sniff, download IP-Sniff, IP-Sniff free download, IP Traffic, Monitor IP, IP Scanner, Traffic, Monitor, Scan |
| Users' rating (5 rating) |
Using IP-Sniff Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of IP-Sniff on rapidshare.com, depositfiles.com, megaupload.com etc.
All IP-Sniff download links are direct IP-Sniff full download from publisher site or their selected mirrors.
Avoid: vulnerabilities oem software, old version, warez, serial, torrent, IP-Sniff keygen, crack.
Consider: IP-Sniff full version, vulnerabilities full download, premium download, licensed copy.