Invent Upshot 1.2.0.66
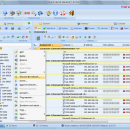
Invent Upshot is a new, feature rich and low TCO, agent-free network discovery, hardware & software inventory and remote tool, with which you can manage a single PC to several home and corporate networks in a few minutes (hard wired or wireless). ...
| Author | Aplixio |
| License | Trialware |
| Price | $42.00 |
| Released | 2010-10-25 |
| Downloads | 273 |
| Filesize | 10.30 MB |
| Requirements | |
| Installation | Instal And Uninstall |
| Keywords | Network Inventory, Remote Inventory, Network Chart, Inventory, Network, Remote |
| Users' rating (5 rating) |
Using Invent Upshot Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Invent Upshot on rapidshare.com, depositfiles.com, megaupload.com etc.
All Invent Upshot download links are direct Invent Upshot full download from publisher site or their selected mirrors.
Avoid: weak oem software, old version, warez, serial, torrent, Invent Upshot keygen, crack.
Consider: Invent Upshot full version, weak full download, premium download, licensed copy.