MySQL 9.0.1 Innovation
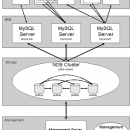
... a distributed architecture that ensures data is always accessible, making it ideal for mission-critical workloads. With features like automatic sharding, in-memory storage, and seamless scalability, MySQL Cluster supports large-scale deployments while maintaining ACID compliance. Its robust replication and fault-tolerance capabilities empower businesses ... ...
| Author | MySQL AB |
| License | Open Source |
| Price | FREE |
| Released | 2024-07-23 |
| Downloads | 1274 |
| Filesize | 385.00 MB |
| Requirements | |
| Installation | Instal And Uninstall |
| Keywords | cluster, database, share, MySQL, distributed system, MySQL database, high availability, database software, scalability |
| Users' rating (23 rating) |
Using MySQL Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of MySQL on rapidshare.com, depositfiles.com, megaupload.com etc.
All MySQL download links are direct MySQL full download from publisher site or their selected mirrors.
Avoid: unauthorized access oem software, old version, warez, serial, torrent, MySQL keygen, crack.
Consider: MySQL full version, unauthorized access full download, premium download, licensed copy.